Advertisement
When people think about connecting to remote computers over a network, two tools often come to mind — SSH and Telnet. Both allow users to log into another machine and manage it as if they were sitting right there. However, what happens under the hood between the two could not be more different. One was built for a simpler time when networks were trusted, and the other grew out of the need to protect data from prying eyes. Understanding the difference between SSH and Telnet is key to knowing which one to use in today’s connected world.
Telnet was introduced in the early 1970s when the internet as we know it did not exist, and networks were small, controlled, and assumed secure. It was designed as a protocol that lets a user establish a text-based communication session with a remote host. When you use Telnet, your keystrokes are sent over the network as plain text, and so is everything sent back from the server. Anyone intercepting the traffic can read usernames, passwords, and command output easily. Telnet opens a TCP connection on port 23 and streams characters between client and server without encryption or proper validation.
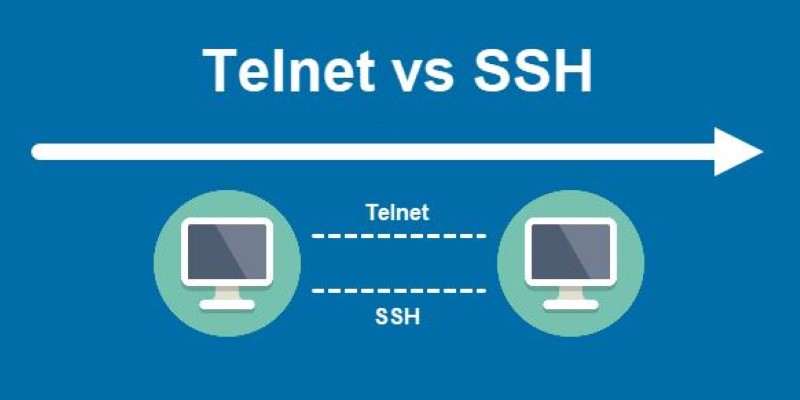
SSH, short for Secure Shell, was created to fix this exact problem. Introduced in the mid-1990s, SSH adds encryption and authentication to remote shell sessions. It uses cryptographic algorithms to secure the connection, preventing attackers from reading or tampering with the data in transit. SSH operates over TCP as well, but typically on port 22, and before sending any actual data, the client and server perform a cryptographic handshake to establish an encrypted channel. From there, all information — commands, output, even the login process — is encrypted, making it nearly impossible for an eavesdropper to extract anything useful. SSH also supports features such as public key authentication, which allows stronger and more flexible ways to prove identity than just a password.
In short, while both SSH and Telnet offer a way to access a command-line interface on a remote machine, SSH wraps every interaction in strong cryptography, whereas Telnet leaves everything exposed.
The most obvious difference between SSH and Telnet lies in how secure they are. Telnet does not offer any security beyond requiring a password to log in. But because that password and every subsequent keystroke are sent in cleartext, anyone with access to the network traffic can steal credentials, see commands, and even inject malicious commands into the session. This was acceptable decades ago when networks were isolated, but in today’s world of public and shared networks, it leaves systems open to easy attacks.
SSH was developed precisely to address these risks. It's an encrypted tunnel that not only hides all information from potential eavesdroppers but also verifies that the server you're connecting to is really the one you intend to reach. This prevents man-in-the-middle attacks, where an attacker intercepts and alters communications between client and server. SSH also supports stronger authentication methods, like using cryptographic keys instead of passwords, which adds another layer of protection.
From a cybersecurity perspective, using Telnet on an open or even semi-public network is highly discouraged, and many modern operating systems don't even enable a Telnet server by default anymore. SSH, by contrast, is widely recommended for remote administration tasks, file transfers, and even port forwarding, as it provides strong security without much additional setup.
While the security difference is the most talked about, SSH and Telnet also differ in functionality. Telnet is extremely lightweight and simple, which made it popular in its time. It requires minimal computing resources and works on just about any system, even very old or resource-constrained ones. However, its simplicity is also its limitation — it was designed solely for plain terminal access and doesn’t support additional capabilities.

SSH, while slightly heavier due to the cryptographic overhead, brings along more features that make it much more versatile. SSH can forward ports, allowing secure tunneling of other services over the encrypted connection. It can also transfer files using secure protocols such as SCP (Secure Copy) or SFTP (Secure File Transfer Protocol), all using the same secure session. Many SSH implementations also support multiplexing, which allows multiple logical sessions over a single physical connection, saving resources and improving performance.
Even in terms of user experience, SSH provides better support for terminal capabilities, such as handling terminal window size changes and various character encodings, which makes working on modern systems more seamless.
For anyone concerned about cybersecurity — which is to say anyone operating in today's networked environment — SSH is the clear choice. Telnet is still occasionally used in controlled environments where networks are fully isolated and simplicity is desired, but even then, it's becoming rare. Many organizations have disabled Telnet entirely on their servers and devices, replacing it with SSH even for internal use. SSH's encryption and authentication mechanisms make it a much safer option. In contrast, its extra features make it more practical and efficient for real-world use.
For educational purposes or working with legacy hardware, Telnet might still show up from time to time. But it should only ever be used with full awareness of the risks, and only when there’s no other alternative. SSH is designed with modern threats in mind, which is why it has become the standard for remote administration, even outside traditional Unix and Linux systems.
The difference between SSH and Telnet shows how networking priorities have shifted. Telnet belongs to a time when networks were trusted and security was minimal. SSH emerged to protect sensitive data from common threats. Though similar in purpose, their workings reflect opposite approaches — Telnet is exposed, SSH is secure. Choosing between them affects how well your data and systems are protected today. SSH remains the safer, more capable option, while Telnet reminds us how much cybersecurity has advanced and why secure communication is now a necessity, not a luxury.
Advertisement

Discover ten easy ways of using ChatGPT to analyze and summarize complex documents with simple ChatGPT prompts.
Snowflake's acquisition of Neeva boosts enterprise AI with secure generative AI platforms and advanced data interaction tools

Get full control over Python outputs with this clear guide to mastering f-strings in Python. Learn formatting tricks, expressions, alignment, and more—all made simple
How IonQ advances AI capabilities with quantum-enhanced applications, combining stable trapped-ion technology and machine learning to solve complex real-world problems efficiently
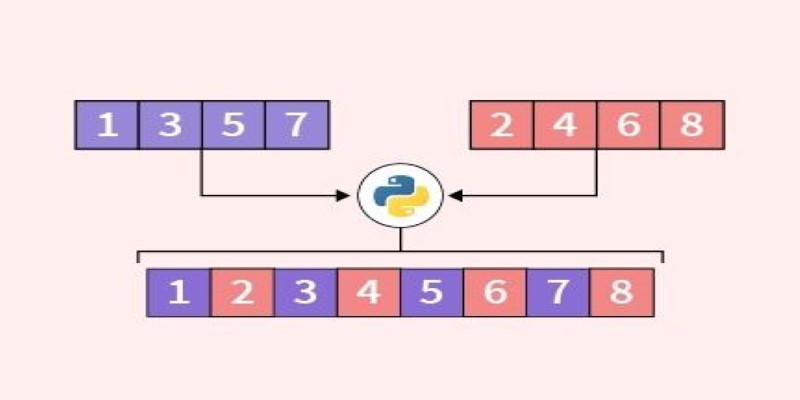
Looking for the best way to merge two lists in Python? This guide walks through ten practical methods with simple examples. Whether you're scripting or building something big, learn how to combine lists in Python without extra complexity

Discover the best AI art generator tools available today. Learn how you can create AI art from text prompts using powerful, easy-to-use platforms suited for beginners and pros alike

Discover execution speed differences between C and Rust. Learn benchmarks, optimizations, and practical trade-offs for developers

How benchmarking text generation inference helps evaluate speed, output quality, and model inference performance across real-world applications and workloads

Ready to make computers see like humans? Learn how to get started with OpenCV—install it, process images, apply filters, and build a real foundation in computer vision with just Python
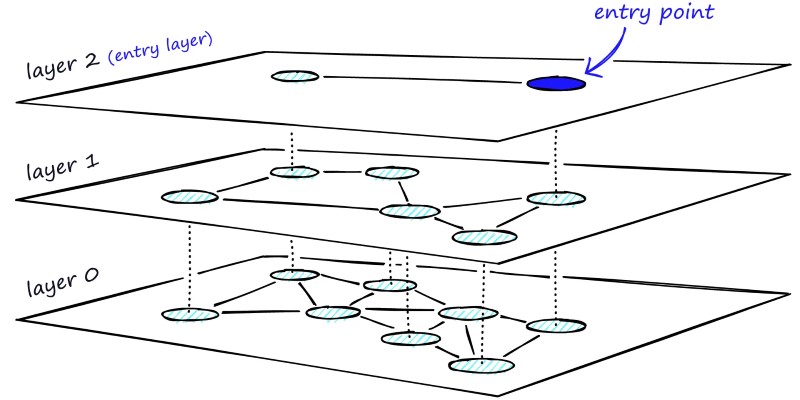
Learn how HNSW enables fast and accurate approximate nearest neighbor search using a layered graph structure. Ideal for recommendation systems, vector search, and high-dimensional datasets

An AI health care company is transforming diagnostics by applying generative AI in radiology, achieving a $525M valuation while improving accuracy and supporting clinicians

Nvidia is set to manufacture AI supercomputers in the US for the first time, while Deloitte deepens agentic AI adoption through partnerships with Google Cloud and ServiceNow